Why 92% of Enterprises Are Blind to the 2025 “Injection Attack” Crisis
A strategic intelligence briefing on the collapse of digital identity and the industrialization of synthetic fraud
The era of “seeing is believing” didn’t just end in 2025; it was liquidated. For decades, the global financial system relied on a singular, tacit assumption: that the voice on the phone or the face on the video call belonged to a verified human entity. The $25 million extraction from a multinational firm in Hong Kong—facilitated not by a hacker in a hoodie, but by a conference call populated entirely by deepfake recreations of the company’s own C-suite—was not an anomaly. It was a proof-of-concept for a new asset class of cybercrime.
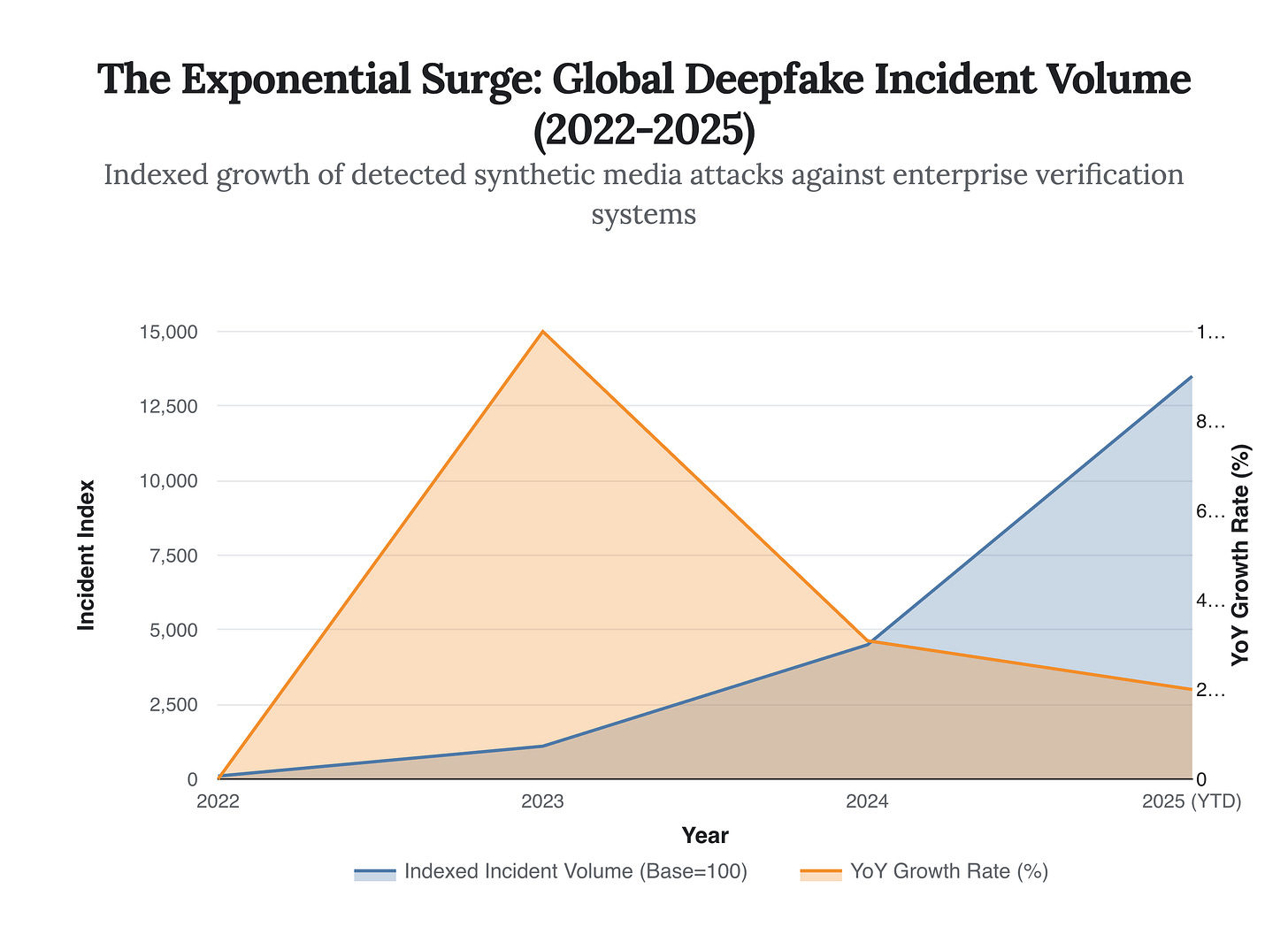
As we close 2025, the data is unequivocal. We are no longer dealing with the “misinformation” threat of 2020, where the primary risk was reputational damage or political polarization. We have entered the Extraction Phase. Synthetic media has mutated from a tool of influence into a precision weapon for financial solvency attacks. The cost of contact center fraud driven by deepfakes is projected to hit $44.5 billion this year, yet 92% of enterprise security stacks remain optimized for a threat landscape that no longer exists.
This chart is not merely a trend line; it is a portrait of failure. The verticality of the 2024-2025 curve represents the democratization of Crime-as-a-Service (CaaS). Access to high-fidelity voice cloning and real-time video swapping tools has plummeted in cost, allowing non-technical actors to execute state-level deception campaigns. The strategic implication is severe: the barrier to entry for defrauding a Fortune 500 company has dropped from “advanced persistent threat” capabilities to a $50 monthly subscription.
The Shift to “Injection Attacks”: The Camera is the Compromise
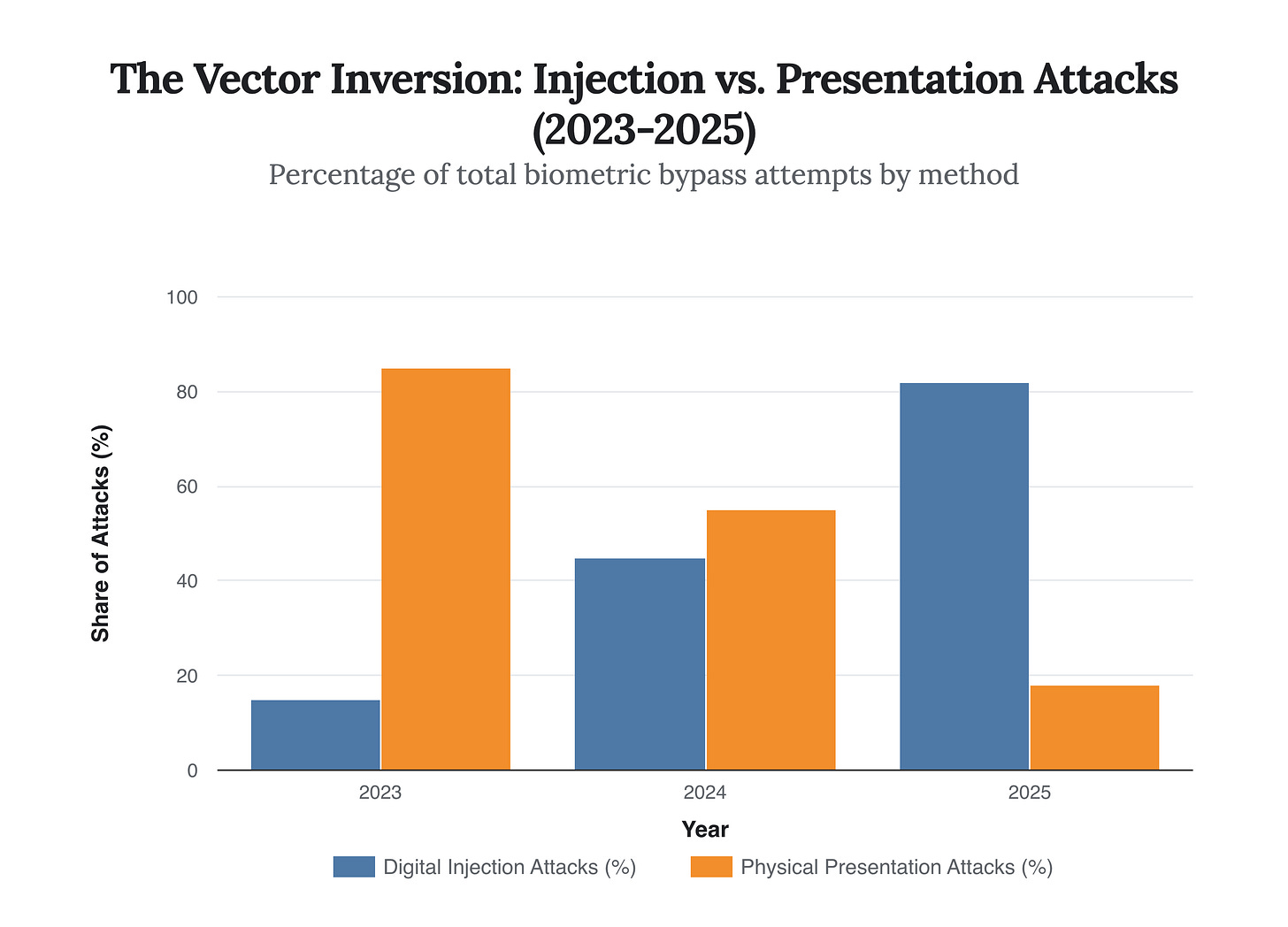
The most dangerous misconception in boardrooms today is the belief that biometric security—FaceID, video KYC (Know Your Customer), and voice verification—is a firewall. In 2025, it is a sieve. The threat vector has shifted fundamentally from Presentation Attacks (holding a mask or phone up to a camera) to Digital Injection Attacks.
In an injection attack, the physical camera lens is bypassed entirely. Malicious code injects pre-rendered or real-time synthetic media directly into the data stream. The security system “sees” the face it expects because the data feed itself has been hijacked. Our analysis of 2025 attack vectors shows a complete inversion of the threat landscape.
The strategic takeaway here is chilling: hardware trust is dead. If your security protocol relies on the assumption that the video feed is originating from the physical device’s sensor, you are already compromised. The 82% dominance of injection attacks indicates that fraudsters have industrialized the bypass of standard liveness detection APIs. They are not trying to fool the camera; they are replacing the reality the camera perceives.
The Solvency Risk: Sector Vulnerability
While the media focuses on celebrity likeness theft, the real bleeding is occurring in high-volume transactional sectors. Financial services and crypto exchanges have become