The $75 Million Warning: Why the Ransom Economy Is Abandoning Mass-Market Crime
A strategic analysis of the “Volume-Value Paradox” and the rise of boutique extortion
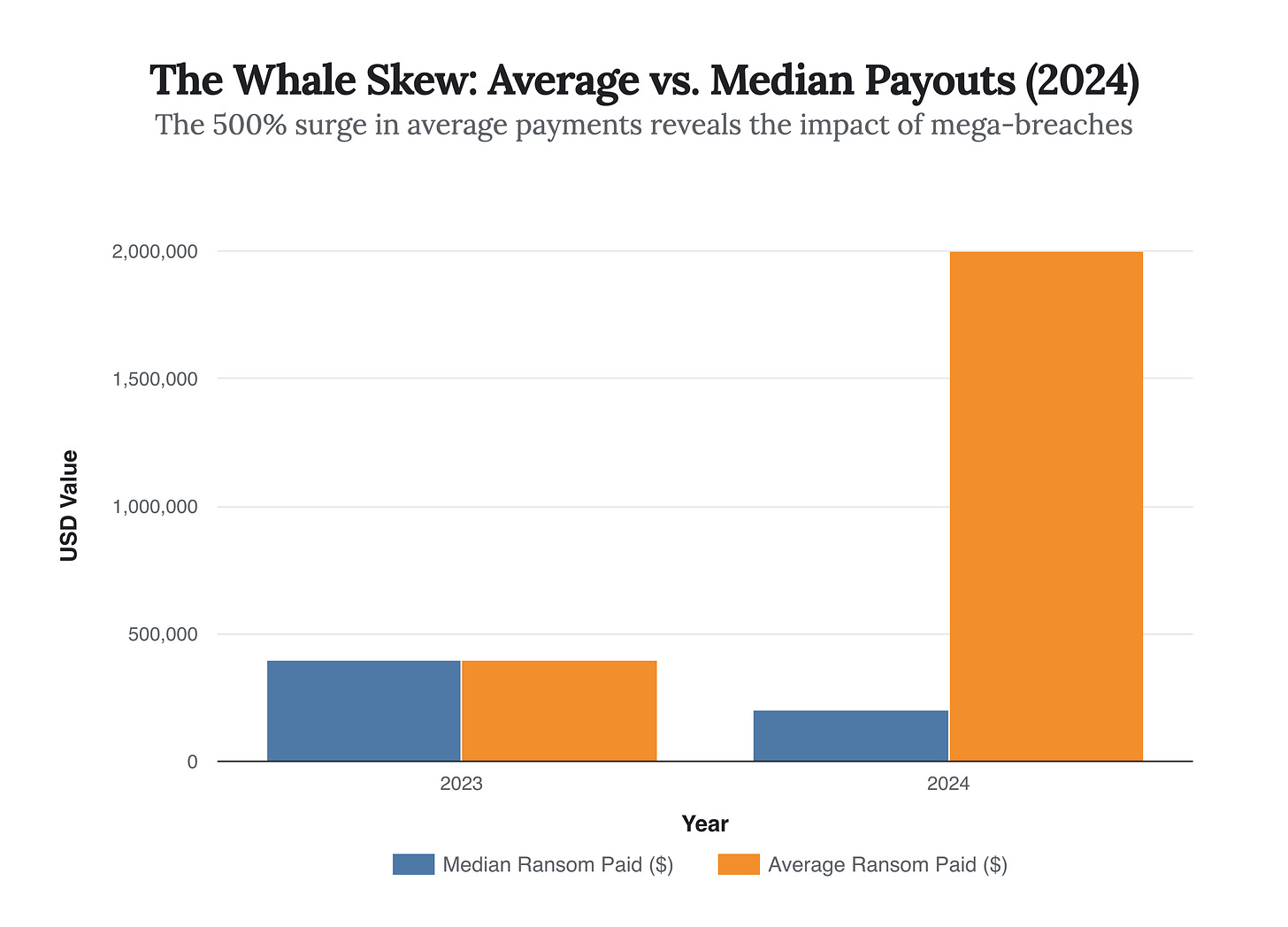
The Ransom Economy has entered a phase of aggressive gentrification. For the past decade, ransomware was a volume game—a digital dragnet cast wide to catch small-to-medium enterprises (SMEs) with poor hygiene. That era is dead. The latest intelligence from late 2024 and early 2025 confirms a structural decoupling: while the raw number of attacks has surged by 34%, the percentage of victims paying the ransom has collapsed to a historic low of ~28%. Yet, the average ransom payment has skyrocketed 500% to nearly $2 million, capped by a record-breaking $75 million payout by a Fortune 50 entity to the Dark Angels group.
This is the Volume-Value Paradox. We are witnessing the industrial maturity of cyber extortion. Attackers are shedding the operational overhead of managing thousands of small victims in favor of “Big Game Hunting”—targeting fewer, wealthier organizations with bespoke, high-pressure campaigns. They are trading scale for yield. This briefing deconstructs the new economic engine of ransomware, analyzing the shift from encryption to pure extortion, the collapse of dwell times, and the weaponization of regulatory transparency.
The Gentrification of Cybercrime: Deconstructing the “Whale” Strategy
The most dangerous misconception in boardrooms today is that the decline in ransom payment rates (the percentage of victims who pay) signals a victory for defense. It does not. It signals a shift in the adversary’s business model. The Ransom Economy has bifurcated into two distinct tiers: a chaotic, low-margin tier of automated attacks against SMEs, and a highly professionalized, high-margin tier targeting critical infrastructure and global conglomerates.
The Bifurcation of Risk
The data reveals a market in extreme disequilibrium. While the median ransom demand hovers around $200,000—reflecting the long tail of automated attacks—the average payment has detached completely, driven by “mega-breaches” like the Change Healthcare incident and the Dark Angels extortion. This skew indicates that while fewer companies are paying, the ones that do are paying exponentially more.
This data suggests that the “middle class” of ransomware victims—those who used to pay $50,000 to $100,000 to unlock their files—are increasingly refusing to pay, emboldened by better backups and cyber insurance mandates. In response, elite threat actors have abandoned this demographic to focus exclusively on targets where downtime costs exceed $10 million a day.
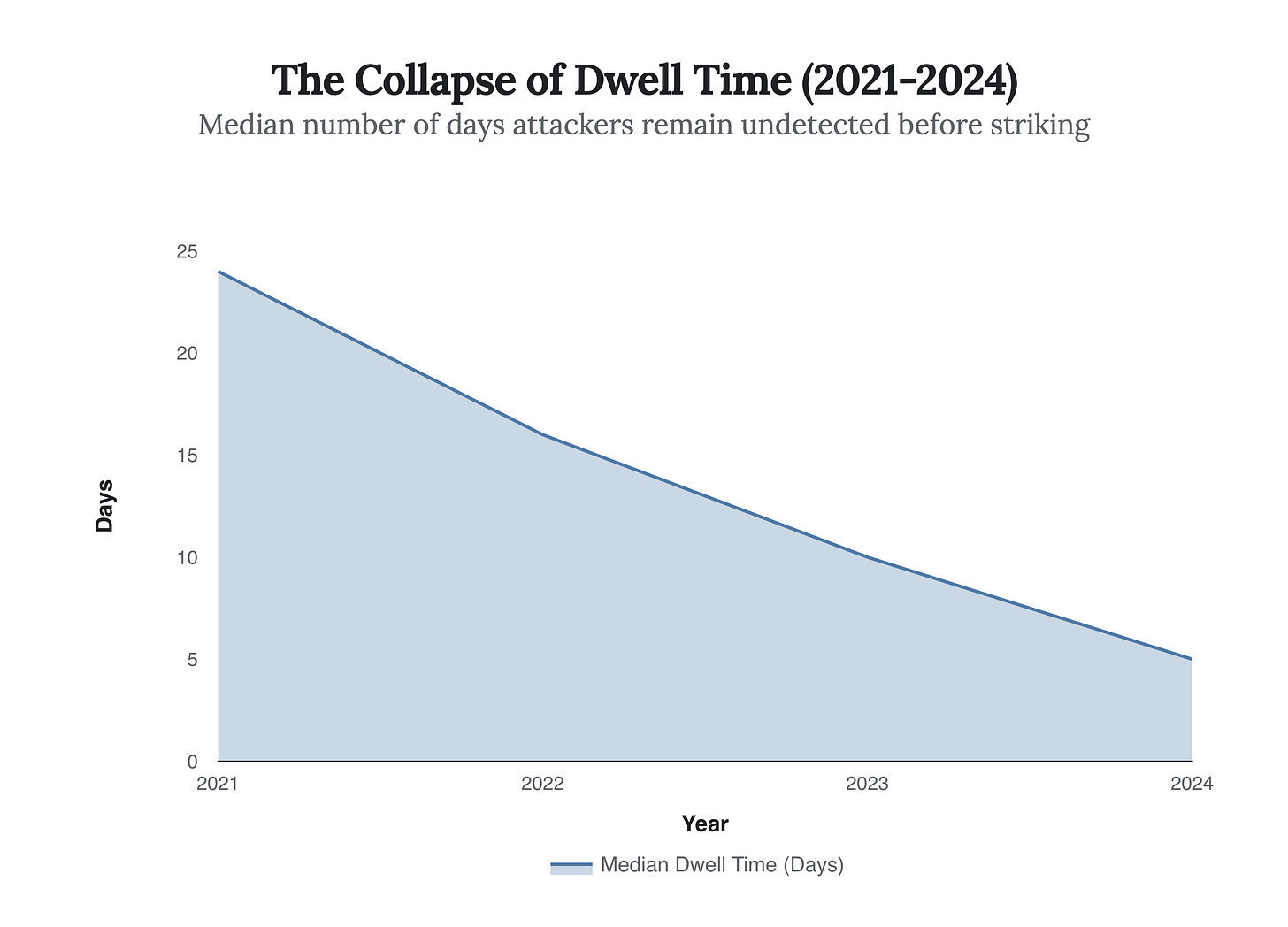
The Speed of Ruin: The Collapse of Dwell Time
The operational tempo of the Ransom Economy has accelerated beyond the decision-making cycle of most corporate incident response teams. In 2021, the median “dwell time”—the time an attacker spends inside a network before striking—was over three weeks. Today, it is under one week, with some attacks executing data exfiltration within 24 hours of initial compromise.
The Automation of Intrusions
This compression is driven by the rise of Initial Access Brokers (IABs) and the automation of vulnerability scanning. Attackers no longer “hack” in; they log in using credentials purchased from IABs or exploit zero-day vulnerabilities (like those in MOVEit or various VPN concentrators) at scale. The window for detection and containment has effectively closed for organizations relying on manual log review.
The strategic implication is profound: Prevention is the only viable containment. Once an adversary is inside, the time-to-ransom is now shorter than