The 15.72 Terabit Salvo: How a Single Azure Endpoint Survived the Largest DDoS Attack in Cloud History
In the silent, digital trenches of the global internet, a new world record was set on October 24, 2025. It wasn’t a feat of engineering or a breakthrough in connectivity, but an act of brute force on an unprecedented scale. A single, unsuspecting endpoint in a Microsoft Azure datacenter in Australia was hammered by a distributed denial-of-service (DDoS) attack that peaked at 15.72 terabits per second (Tbps).
Originating from the ‘Aisuru’ botnet, a sprawling network of over 500,000 compromised home routers and Internet of Things (IoT) devices, the attack represented a quantum leap in the scale of cyber threats. Yet, for the targeted customer, service remained uninterrupted. The attack was absorbed and neutralized by Azure’s automated defenses, a testament to the immense, behind-the-scenes infrastructure required to keep the cloud operational. This event was not an anomaly; it was a declaration. It signals the dawn of the hyper-scale DDoS era, where attack volumes are scaling with the internet itself, driven by a confluence of geopolitical tensions, the proliferation of insecure IoT devices, and the democratization of powerful attack tools. This briefing deconstructs this new reality, analyzing the forces driving this escalation and the strategic calculus required to maintain digital resilience in the face of terabit-scale threats.
The Anatomy of a Hyper-Scale Siege
The 15.72 Tbps event provides a stark blueprint for the modern DDoS threat landscape. It’s a landscape defined not just by sheer volume, but by the increasing sophistication of threat actors and the evolving tactics they employ to overwhelm defenses. Understanding these components is critical for any leader whose operations depend on the cloud.
From Terabits to Tens of Terabits: The Exponential Threat Vector
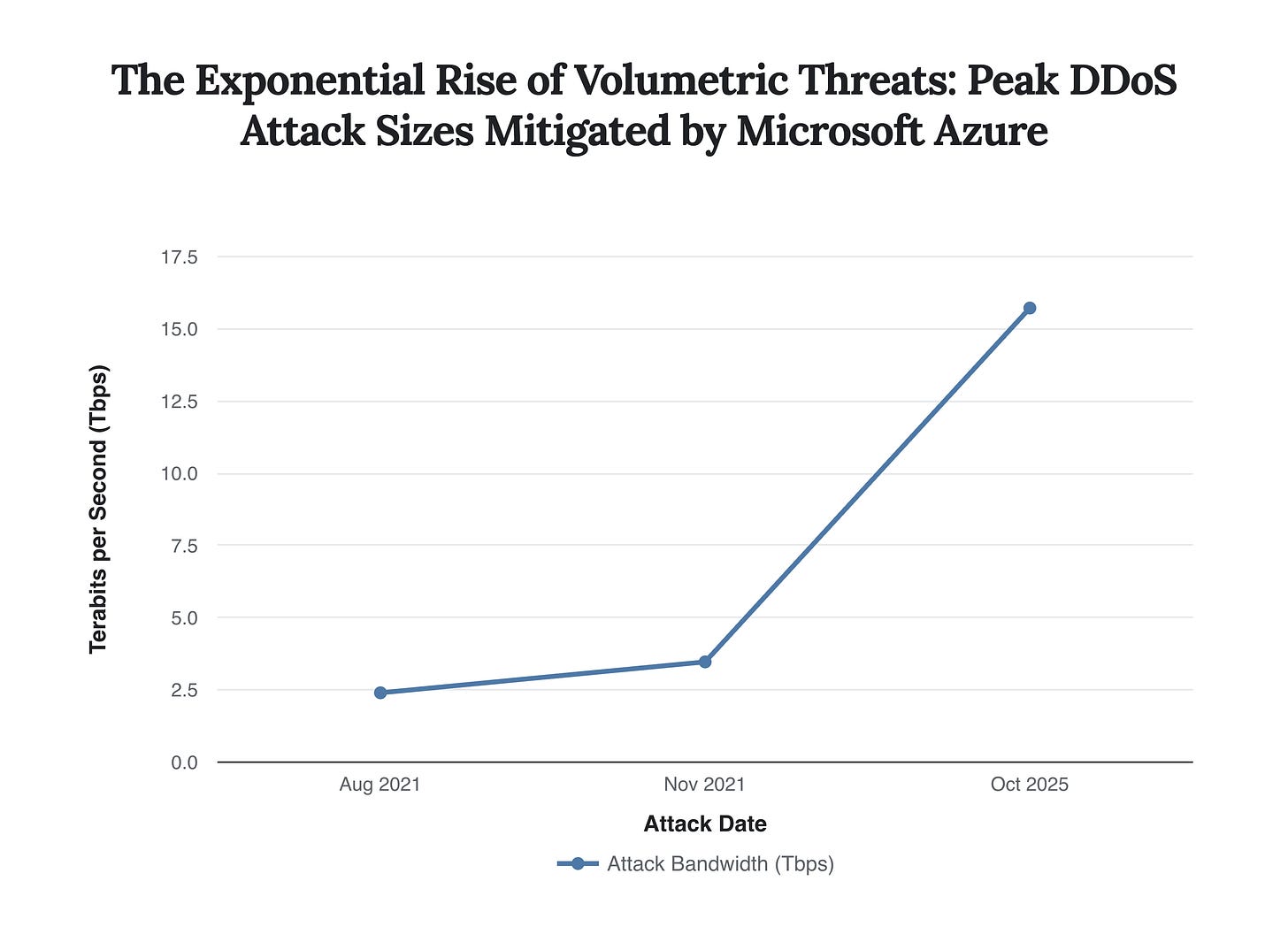
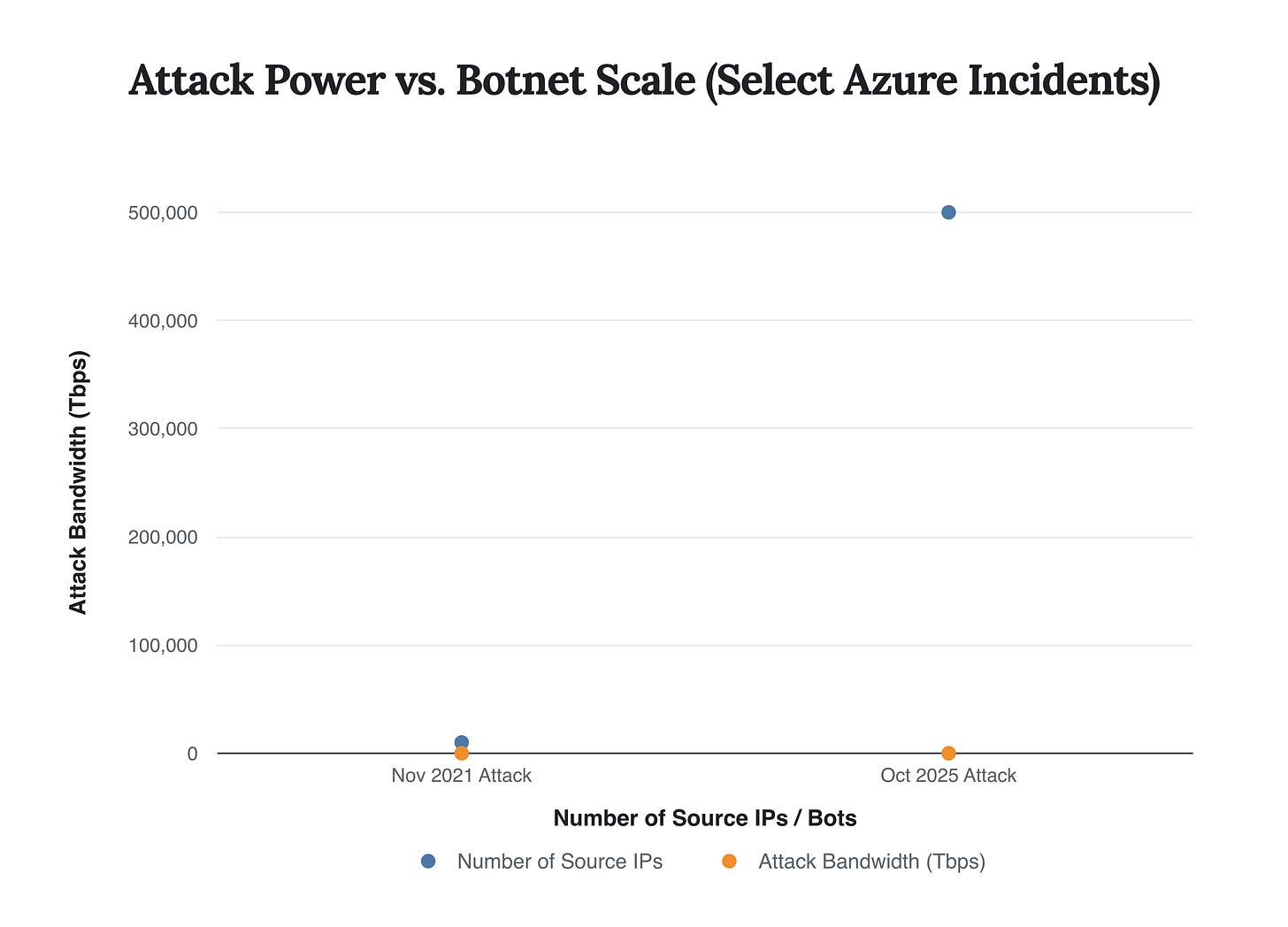
The escalation in attack bandwidth is staggering. While Microsoft’s mitigation of a 2.4 Tbps attack in August 2021 was a landmark event, followed by a then-record 3.47 Tbps attack in November 2021, the October 2025 assault represents a more than four-fold increase in just four years. This exponential growth is not a temporary spike but a sustained trend, mirroring the rapid expansion of global internet capacity and the explosion of high-bandwidth, low-security consumer devices.
The peak bandwidth of DDoS attacks targeting Microsoft Azure has seen a dramatic, exponential increase, culminating in the record-breaking 15.72 Tbps attack in late 2025, highlighting the rapidly scaling capabilities of modern botnets.
The Arsenal: Shifting Protocols and Multi-Vector Assaults
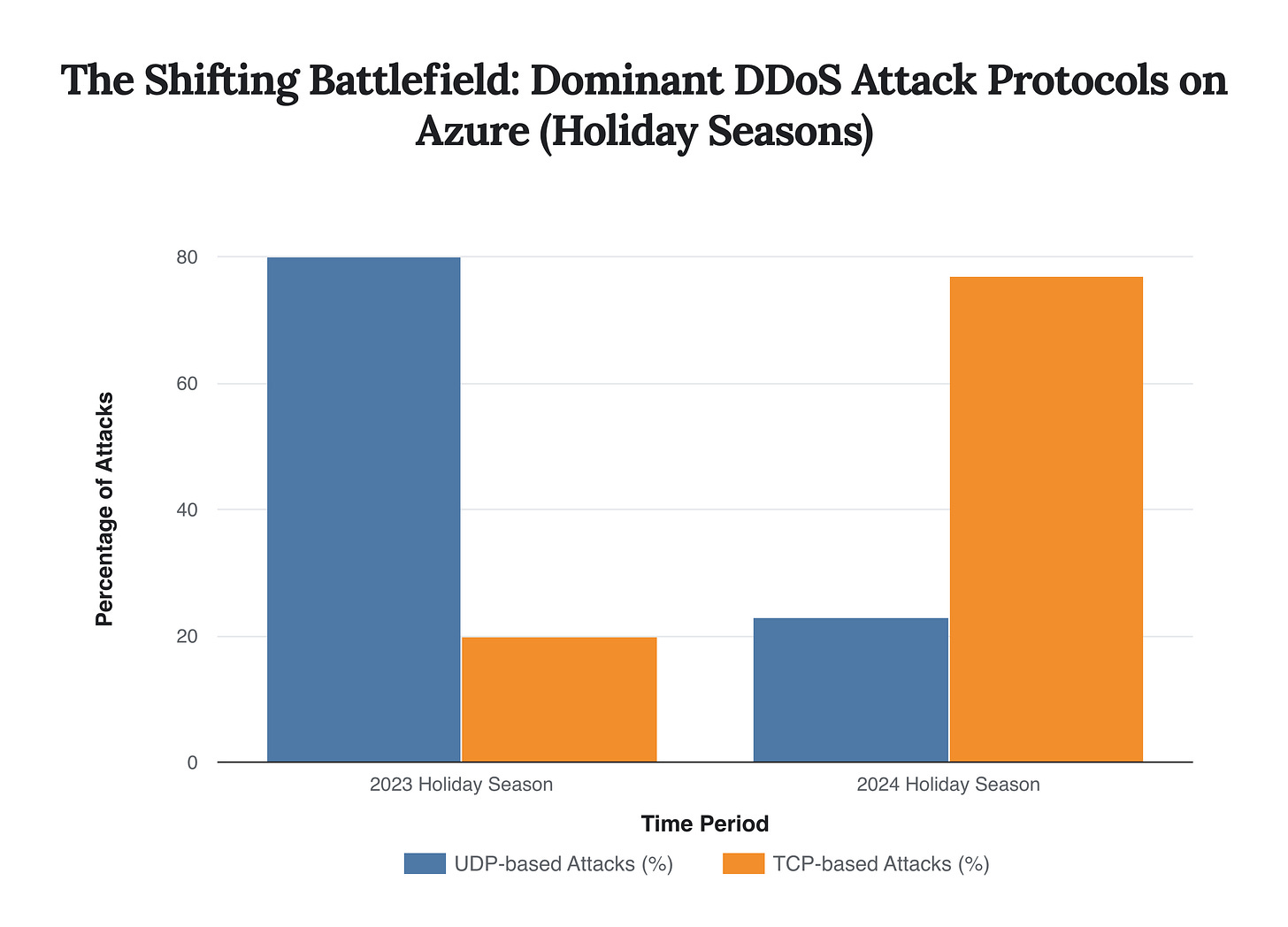
Threat actors are continuously refining their tactics, shifting between different attack protocols to probe for weaknesses. The 15.72 Tbps attack was a massive User Datagram Protocol (UDP) flood, a classic volumetric attack designed to saturate a target’s bandwidth with immense traffic. However, broader trends show a dynamic shift. During the 2024 holiday season, Microsoft observed that 77% of attacks were Transmission Control Protocol (TCP)-based, a stark reversal from the previous year when UDP attacks dominated the landscape. State-affiliated groups like ‘Anonymous Sudan’ (tracked by Microsoft as Storm-1359) favor more sophisticated Layer 7 attacks, which mimic legitimate user traffic to bypass traditional network defenses and exhaust application resources through methods like HTTP(s) floods and Slowloris attacks.
Analysis of recent holiday seasons shows a dramatic tactical shift by attackers, moving from a majority of UDP-based volumetric attacks in 2023 to a heavy focus on TCP-based attacks in 2024.
The New Belligerents: Botnets, Hacktivists, and Geopolitics
The forces behind these attacks are a complex mix of criminal enterprises, state-sponsored actors, and ideologically motivated hacktivists. The lines are increasingly blurred as their tools and motivations overlap, creating a volatile and unpredictable threat environment.
The Rise of the IoT Super-Botnet: Aisuru
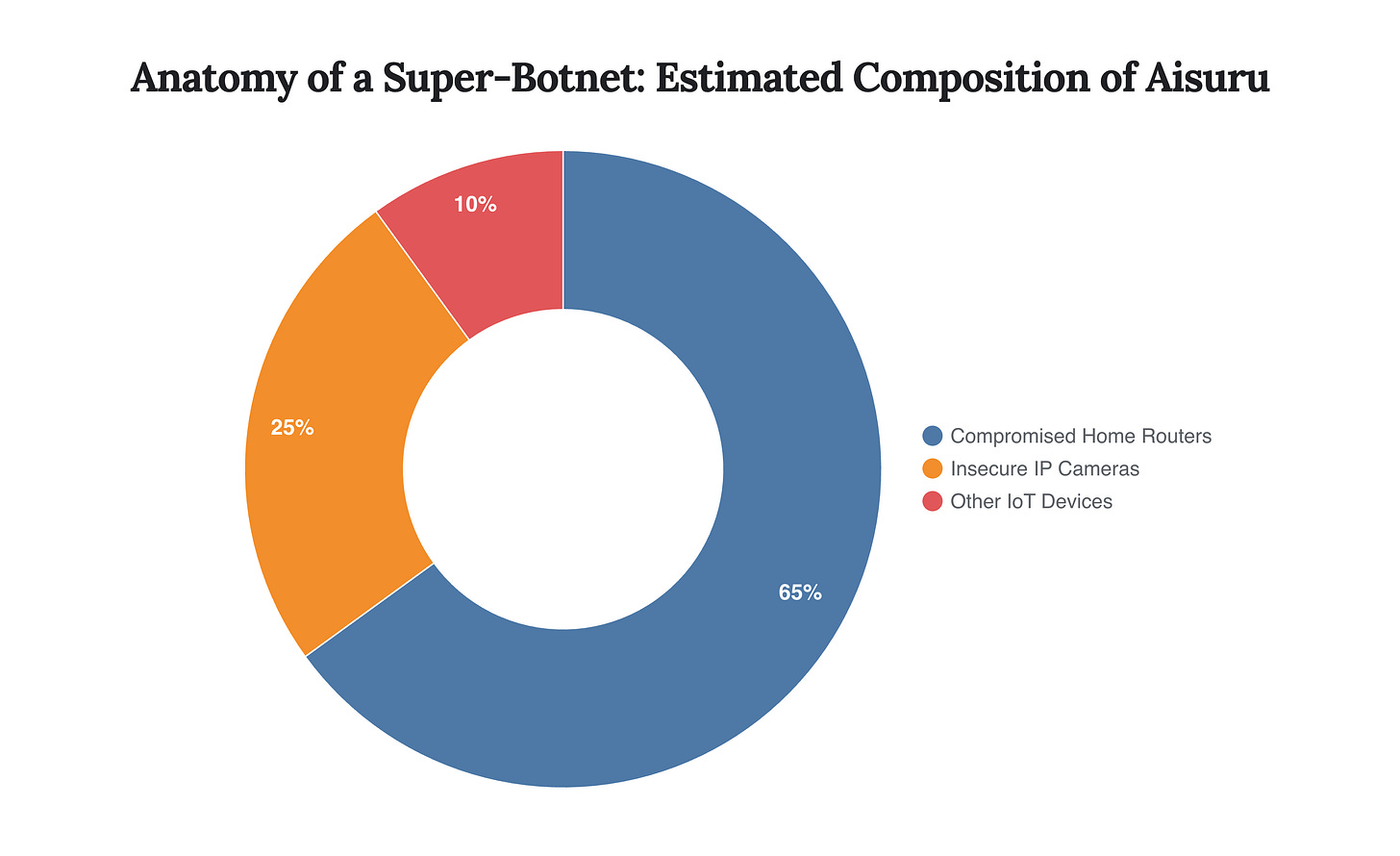
The Aisuru botnet, responsible for the 15.72 Tbps attack, represents the new apex predator of the internet. A variant of the infamous Mirai botnet, Aisuru amasses its power by compromising hundreds of thousands of poorly secured IoT devices, primarily consumer-grade routers and security cameras. These devices, often shipped with default passwords and rarely updated, provide the perfect fodder for a globally distributed attack network. The botnet’s operators then sell access to this formidable weapon as a ‘DDoS-for-hire’ service, democratizing the ability to launch infrastructure-crippling attacks for as little as a few hundred dollars.
“As we highlighted in the 2021 Microsoft Digital Defense Report, the availability of DDoS for-hire services as well as the cheap costs—at only approximately $300 USD per month—make it extremely easy for anyone to conduct targeted DDoS attacks.”
The Aisuru botnet primarily consists of compromised consumer-grade hardware, with home routers and IP cameras forming the vast majority of its attack capacity, highlighting a critical vulnerability in the consumer electronics supply chain.
Hacktivism as a Geopolitical Tool
DDoS attacks have firmly cemented their place as a tool of statecraft and geopolitical protest. Groups like Anonymous Sudan, widely believed to be a Russian state-aligned operation, launched a series of disruptive attacks against Microsoft services, including Outlook and Azure, in 2023. These attacks were explicitly framed as retaliation for perceived Western involvement in geopolitical conflicts. This trend is global, with Microsoft noting significant spikes in DDoS activity coinciding with major political events, such as India’s national elections in June 2024. The motivation is no longer just financial; it is about disruption, publicity, and projecting power in the digital domain.
The Ceaseless War: Quantifying Azure’s Daily Defense
The record-breaking attacks grab headlines, but the reality for Azure’s security teams is a perpetual state of defense against a constant barrage of lower-level threats. Microsoft’s infrastructure mitigates thousands of unique attacks every single day, a number that has been steadily climbing.
The Daily Attack Volume
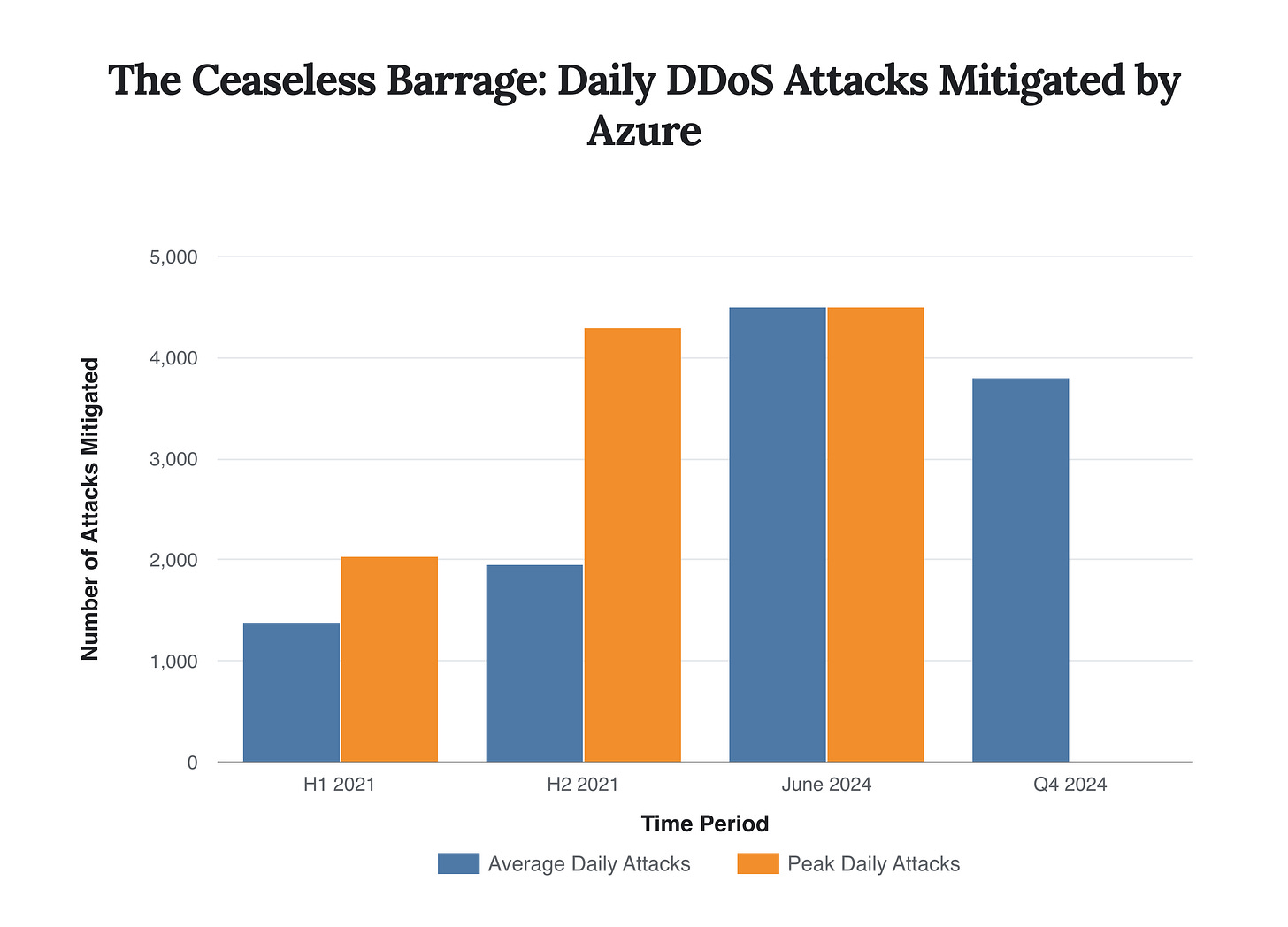
In the first half of 2021, Microsoft mitigated an average of 1,392 attacks per day. By the second half of that year, the average rose 40% to 1,955 daily attacks. Fast forward to 2024, and the scale has intensified further, peaking at approximately 4,500 attacks per day in June and averaging around 3,800 during the subsequent holiday season. This relentless pressure requires a defense-in-depth strategy that is both automated and massively scalable.
The volume of daily DDoS attacks mitigated by Azure has shown a consistent and significant increase, with peak volumes in mid-2024 reaching more than double the average rates seen in 2021.
The Strategic Implications: The High Cost of Digital Disruption
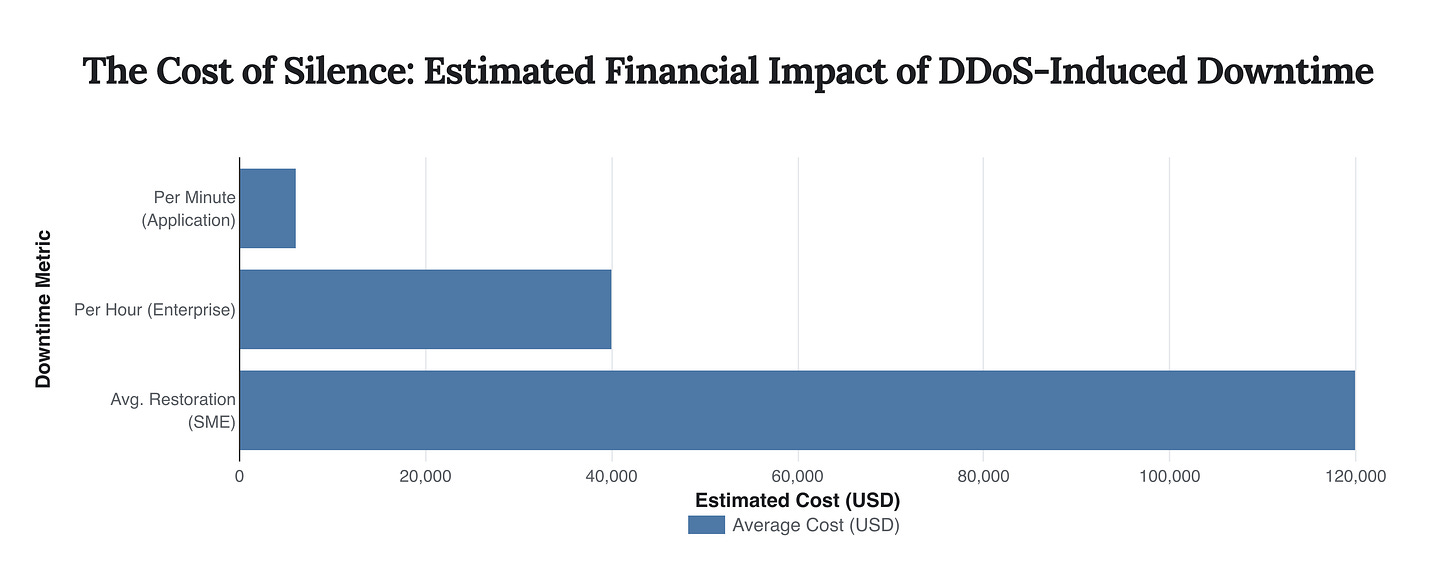
For industry leaders and policymakers, the core issue is the tangible business and economic risk posed by these attacks. Downtime is not a mere inconvenience; it is a direct and substantial financial drain. Studies have placed the average cost of downtime from a successful application DDoS attack at over $6,000 per minute. For larger enterprises, this can translate to nearly $40,000 per hour. These figures don’t even account for the long-term damage to brand reputation, customer trust, and potential regulatory scrutiny.
The financial consequences of a successful DDoS attack are severe, ranging from thousands of dollars per minute in lost revenue to over a hundred thousand dollars in average restoration costs for small-to-medium enterprises.
Strategic Foresight: The Future of the DDoS Arms Race
The 15.72 Tbps attack is a watershed moment, but it is not the ceiling. The trends point toward an even more volatile future where attack capabilities continue to outpace the defensive postures of unprepared organizations.
The Coming Wave: AI, 5G, and Hyper-Volumetric Threats
Looking ahead, several factors will fuel the next evolution of DDoS attacks. The integration of AI into botnets will allow for more sophisticated, adaptive attacks that can change vectors in real-time to evade mitigation. The continued rollout of 5G and high-speed fiber will increase the potential bandwidth of each compromised device, making it easier to achieve hyper-volumetric scale. The primary targets will continue to be the industries most dependent on real-time availability.
“Microsoft assessed that Storm-1359 has access to a collection of botnets and tools that could enable the threat actor to launch DDoS attacks from multiple cloud services and open proxy infrastructures. Storm-1359 appears to be focused on disruption and publicity.”
A clear correlation exists between the number of devices in a botnet and its potential attack power. The 50x increase in source IPs between the 2021 and 2025 mega-attacks resulted in a more than 4x increase in destructive bandwidth, demonstrating the critical threat of botnet expansion.
The defense against this future rests on the continued investment in globally distributed, cloud-native protection platforms. The mitigation of the 15.72 Tbps attack was not a stroke of luck; it was the result of a deliberate architectural strategy designed to absorb and scrub malicious traffic at the network edge, far from the customer’s application. For leaders, the key takeaway is that relying solely on on-premises or underscaled solutions is no longer a viable strategy. The scale of the threat now mandates a partnership with hyperscale cloud providers who can leverage their massive global footprint as a defensive shield. The era of the isolated digital fortress is over; survival in the age of terabit-scale attacks depends on collective, cloud-powered resilience.
The digital battlefield is no longer measured in gigabits, but in terabits, and the price of unpreparedness is not just downtime, but irrelevance.